By Prabhudarshan Samal
This article is about a well-illustrated write-up based on hacking activities in an educational temperament and non-abusive intent.
The techniques and resources provided by the article are totally intended for educational purposes. We do not encourage any kind of malignant or malicious activities inspired by this article
Here is the source for the vulnhub machine on which we are going to perform hacking techniques
https://www.vulnhub.com/entry/basic-pentesting-2,241/
Download this machine and install it in the virtual box you can get either torrent or zip file of it but downloading the .ova file and configuring and installing it on the oracle virtual box will be smooth sailing.
So before going to the actual core techniques and steps I wish to tell you that please set the network configuration of both the settings to NATnetwork so that the two machines can work in a LAN network and the machines using the same network is hackable.
Now we start our stages to hack it
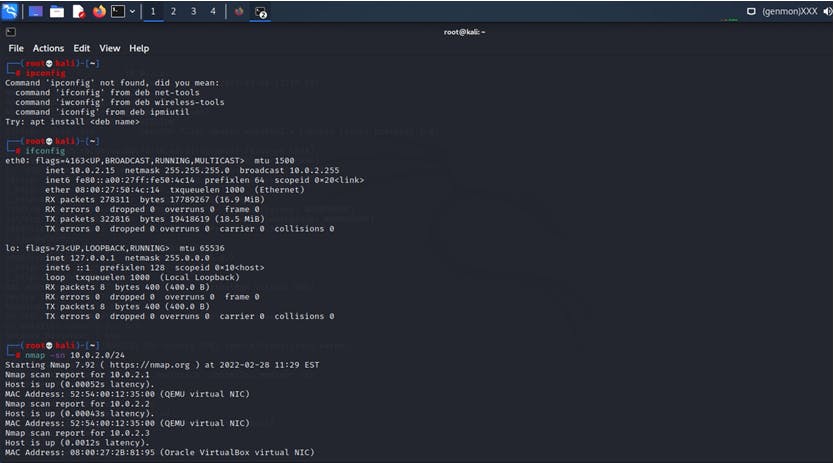
What we tried to perform here is we search for network configuration i.e ipv4 address of the hacker machine and used the command “ifconfig”
This command gives us the ipv4 address of the system and next what we tried is we performed a ping scan using the tool Nmap and went for scanning to the entire network and got some of the hosts.
This command gives us the ipv4 address of the system and next what we tried is we performed a ping scan using the tool Nmap and went for scanning to the entire network and got some of the hosts.
After performing an aggressive scan on each of the trial and error ports we came to know that port 22 which has secure shell ssh service running it also has not achieved encryption so by searching this 10.0.2.6/ as URL on the web we get

Note: Along with the explanation of the ping command and other nmap commands the scanning and enumeration stage is also parallely going.

Now after searching in URL we get a webpage under construction but we need to see the source view so we do right click and avail the view-source option

Wait a minute seems like something is fishy in this comment line it is asking for dev tools so this is our hint we go for dirbuster to obtain the directories of such files

So we find development directory now to find it out we go for 10.0.2.6/development
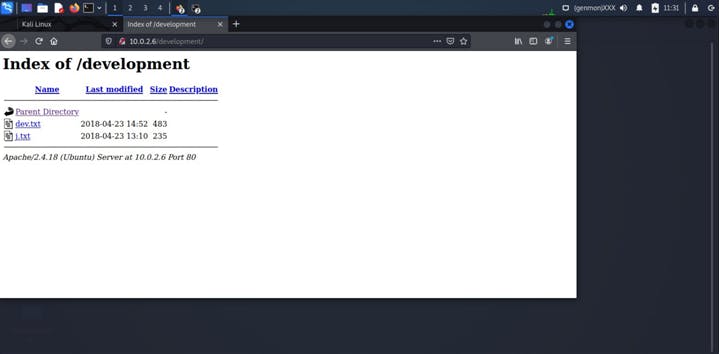
So here is one potential vulnerability discovered two text files are found let us peek into them

It is the content of dev.txt
Now we going to perform gaining and maintaining access stages
Gaining and Maintaining access
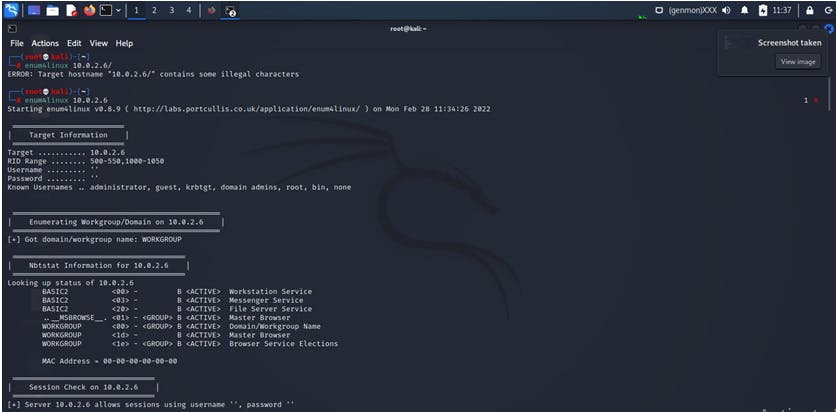
Enum4linux is a tool to scan the ip for getting almost the user count session user information etc it is also an information-gathering tools

So here we found the user of the machine and found the password of the given user jan using bruteforcing tool hydra then by doing so we got the user as “jan” and password as “armando”
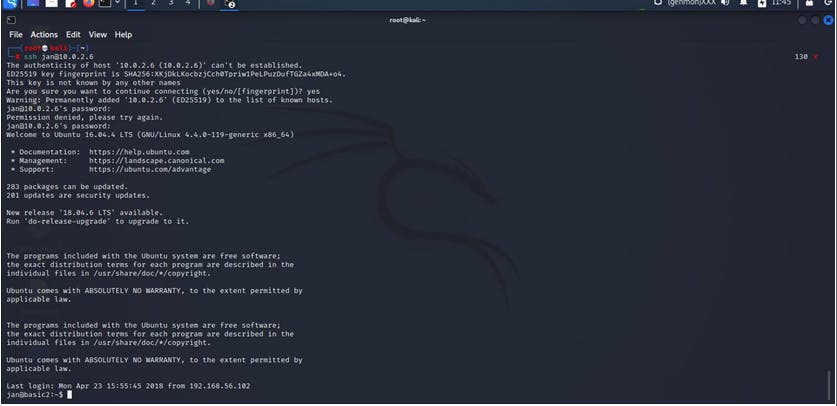
so using the ssh and the username we got to log in into the vulnhub machine and used password “armando”
And boom it's hacked!!!!!

now the we perform various Linux commands to search for password files although we get a pass.bak file yet it's unauthorized to change read write or execute permissions but we found a .ssh script that contains encrypted key

By using the john the ripper tool we created the key into the hash and again it got transformed into a readable key “beeswax”.

Using the id and password using ssh command we got the privilege to gain access on the server now on using super user-mode we access the pass. bak

Finally, after trial and error attempts of various Linux commands we were able to access the target machine and captured the flag.txt that reads the above message.
